Web applications have become an integral part of modern businesses, providing users with convenient access to various services and functionalities. However, the rise in web applications has also led to an increase in security threats and vulnerabilities. In this article, we will explore nine best practices that you need to know to ensure the security of your web applications.
Introduction to Web Application Security
Web application security refers to the protection of web applications from unauthorized access, data breaches, and other malicious activities. It involves implementing robust security measures to safeguard sensitive information, prevent attacks, and maintain the integrity of the application.
Importance of Web Application Security
With the increasing number of cyberattacks targeting web applications, it has become crucial for businesses to prioritize web application security. A security breach can result in financial losses, damage to reputation, loss of customer trust, and legal repercussions. By implementing proper security measures, organizations can mitigate these risks and ensure the smooth functioning of their web applications.
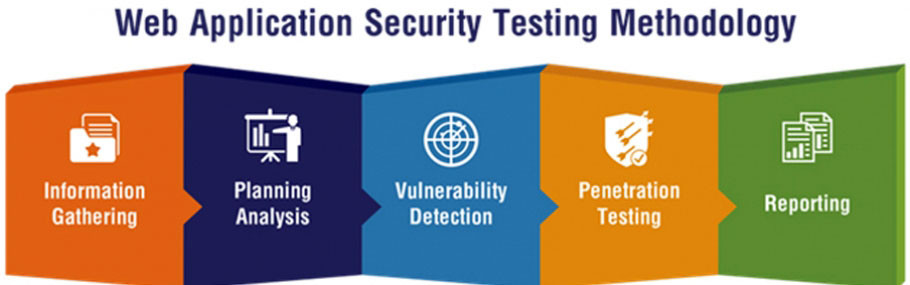
Best Practices for Web Application Security
-
Regularly Update and Patch Your Applications
Keeping your web applications up to date is essential to address any known vulnerabilities and security flaws. Software updates and patches often contain security fixes that can protect your application from the latest threats. Regularly check for updates provided by the application vendors and apply them promptly.
-
Implement Strong Authentication and Authorization Measures
Authentication and authorization are vital components of web application security. Implement multi-factor authentication (MFA) to add an extra layer of security to user accounts. Additionally, enforce strong password policies and utilize secure protocols for user authentication.
-
Secure Data Transmission with HTTPS
Secure data transmission is crucial, especially when sensitive information is being transmitted over the internet. Implement HTTPS (Hypertext Transfer Protocol Secure) to encrypt the data exchanged between the web server and the user’s browser. This ensures the confidentiality and integrity of the transmitted data.
-
Validate and Sanitize User Input
One of the most common security vulnerabilities is the failure to properly validate and sanitize user input. Implement strict input validation mechanisms to prevent various attacks, such as SQL injection and cross-site scripting (XSS). Validate and sanitize user input on the server side and client side to ensure the integrity of the data.
-
Protect Against Cross-Site Scripting (XSS) Attacks
XSS attacks are a prevalent threat to web applications. By injecting malicious scripts into web pages, attackers can compromise user sessions and steal sensitive information. Implement proper input validation and output encoding to prevent XSS attacks.
-
Prevent SQL Injection Attacks
SQL injection attacks occur when an attacker inserts malicious SQL queries into the application’s database. This can lead to unauthorized access, data leakage, and manipulation of the database. Use parameterized queries and prepared statements to prevent SQL injection attacks.
-
Implement Access Controls and Least Privilege
Implement access controls to restrict user access to sensitive functionalities and data. Follow the principle of least privilege, granting users only the minimum privileges required to perform their tasks. Regularly review and update access control policies to ensure they align with the changing security requirements.
-
Use Web Application Firewalls (WAFs)
Web Application Firewalls (WAFs) provide an additional layer of protection by filtering incoming web traffic and blocking malicious requests. Implementing a WAF can help detect and prevent various attacks, including SQL injection, XSS, and CSRF (Cross-Site Request Forgery).
-
Perform Regular Security Audits and Testing
Regularly conduct security audits and testing to identify vulnerabilities and weaknesses in your web applications. This includes performing penetration testing, vulnerability scanning, and code reviews. Address any identified issues promptly to maintain a secure environment.
Educating Developers and Users about Security Risks
Ensuring web application security requires the active involvement of both developers and users. Developers should be educated about secure coding practices, secure development frameworks, and common security vulnerabilities. Users should be educated about the importance of password hygiene, avoiding suspicious links, and being cautious while sharing personal information online.
Common Web Application Security Vulnerabilities
Understanding common web application security vulnerabilities is crucial for effective protection. Some of the most prevalent vulnerabilities include:

-
Cross-Site Scripting (XSS)
XSS vulnerabilities allow attackers to inject malicious scripts into web pages viewed by users. This can lead to session hijacking, data theft, and unauthorized access.
-
SQL Injection
SQL injection vulnerabilities occur when untrusted user input is directly concatenated into SQL queries, allowing attackers to manipulate the database or extract sensitive information.
-
Cross-Site Request Forgery (CSRF)
CSRF vulnerabilities allow attackers to trick authenticated users into performing unintended actions on a web application.
-
Session Hijacking
Session hijacking involves attackers gaining unauthorized access to a user’s session and impersonating them.
-
Server Misconfiguration
Misconfigurations in web servers or application servers can expose sensitive information or allow unauthorized access.
The Role of Secure Coding Practices
Developers play a crucial role in ensuring web application security by following secure coding practices. This includes input validation, output encoding, proper error handling, and adhering to security guidelines and frameworks.
The Need for Regular Security Updates and Patches
Regularly updating and patching your web applications is essential to address newly discovered vulnerabilities and security flaws. Promptly applying security updates and patches help keep your applications secure.
Ensuring Secure Authentication and Authorization
Implementing strong authentication mechanisms, such as multi-factor authentication, and robust authorization controls helps prevent unauthorized access to web applications.
The Importance of Secure Data Transmission
Secure data transmission is crucial to protect sensitive information from interception and unauthorized access. Implementing HTTPS ensures that data exchanged between the server and the client remains confidential and tamper-proof.

Protecting Against OWASP Top 10 Vulnerabilities
The Open Web Application Security Project (OWASP) Top 10 list outlines the most critical web application security risks. By implementing best practices to protect against these vulnerabilities, such as input validation and output encoding, organizations can significantly enhance their application’s security posture.
Implementing Secure Session Management
Secure session management involves properly managing user sessions to prevent session hijacking and ensure session integrity. This includes generating strong session identifiers, implementing session timeouts, and securely storing session-related data.
Web Application Security Testing Tools and Techniques
To ensure the effectiveness of web application security measures, organizations should utilize various testing tools and techniques. This includes vulnerability scanners, penetration testing tools, and code analysis tools to identify and address potential vulnerabilities.
Web Application Firewalls and Intrusion Detection Systems
Web Application Firewalls (WAFs) and Intrusion Detection Systems (IDS) provide additional layers of security by monitoring and analyzing network traffic, detecting suspicious activities, and blocking malicious requests.
Incident Response and Handling
Establishing an effective incident response plan is crucial for quickly detecting, containing, and mitigating security incidents. This includes clear procedures for reporting incidents, investigating the root cause, and implementing remedial actions to prevent future occurrences.
Conclusion
Web application security is of utmost importance in today’s digital landscape. By implementing the nine best practices discussed in this article, organizations can enhance the security of their web applications and protect against potential threats. Remember to regularly update and patch applications, implement strong authentication and authorization measures, secure data transmission, and educate developers and users about security risks. Additionally, conduct regular security audits and testing, address common vulnerabilities, and leverage web application security tools and techniques. By prioritizing web application security, businesses can safeguard their data, maintain customer trust, and ensure the smooth functioning of their web applications.
FAQs
Q. What is web application security?
Web application security refers to the protection of web applications from unauthorized access, data breaches, and other malicious activities by implementing robust security measures.
Q. Why is web application security important?
Web application security is important to mitigate the risks of financial losses, reputational damage, loss of customer trust, and legal repercussions resulting from security breaches.
Q. How can I ensure web application security?
To ensure web application security, you should regularly update and patch applications, implement strong authentication and authorization measures, secure data transmission, and educate developers and users about security risks.
Q. What are common web application security vulnerabilities?
Common web application security vulnerabilities include cross-site scripting (XSS), SQL injection, cross-site request forgery (CSRF), session hijacking, and server misconfiguration.
Q. How can I protect my web application against security vulnerabilities?
You can protect your web application against security vulnerabilities by following secure coding practices, regularly updating and patching your applications, implementing access controls and least privilege, and using web application firewalls (WAFs) and intrusion detection systems (IDS).
